There is a new controversy regarding a feature in the firmware of Bitmain’s Antminer series of Bitcoin miners which allegedly claims that Bitmain can remotely shut down Antminers. This feature was designed and coded by the same team that is responsible for the firmware of Antminers. As the firmware has always been open-source, the feature was never intended to be malicious.
We need to clarify the intention of having this feature. We planned to add this feature to the code to empower customers to control their miners which often times can be hosted outside their premises. This was after more than one incident of miners being stolen from a mining farm or being hijacked by the operator of the mining farm:
- In 2014, around 1,000 Antminers were withheld from the owner by a hosting service provider in Shenyang, China.
- In 2015, around 2,000 units of Antminers were withheld from the owner by a hosting service provider in Georgia.
- In 2017, Bitmain’s own miners were withheld and sold without its consent in Canada.
This feature was intended to allow the owners of Antminer to remotely shut down their miners that may have been stolen or hijacked by their hosting service provider, and to also provide law enforcement agencies with more tracking information in such cases. We never intended to use this feature on any Antminer without authorization from its owner. This is similar to the remote erase or shutdown feature provided by most famous smartphone manufacturers.
However, this feature was never completed. We started to develop this feature since Antminer S7 and wanted to finish its development on the Antminer S9. We hoped to make it a useful feature that we could advertise to our customers. But, due to some technical problems, we were unable to finish the development of this feature and shut down the testing server in December 2016. It is a bug to leave the code there before the feature is fully complete and acknowledged to the users. This bug has now been pointed out in context of Bitcoin’s scaling roadmap debate and has caused considerable misunderstandings within the Bitcoin community. We apologize for this.
Following are the models affected by this bug:
- Antminer S9
- Antminer R4
- Antminer T9
- Antminer L3
- Antminer L3+
Since MITM and DNS hijacks can exploit this bug we would like to apologize to our customers for a degraded level of security caused by this. We should also note that the existing stratum protocol is vulnerable to MITM and DNS hijacks, and that the mining industry needs to work together on design of the next generation mining protocol.
Moving on, we have released the new updated source-code on GitHub and new firmware on our website which removes this bug. We recommend all Antminer owners to upgrade their firmware to the updated firmware from the list below and strongly advise to not download any firmware provided by a third-party which can lead to unexpected outcomes in function and can also be potential phishing attacks.
Antminer S9 firmware
Antminer T9 firmware
Antminer R4 firmware
Antminer L3 firmware
Antminer L3+ firmware
Source code on GitHub
Source-code for Antminer S9, T9 and R4: https://github.com/bitmaintech/bmminer-mix
Source-code for Antminer L3 and L3+: https://github.com/bitmaintech/setup-A8 which includes https://github.com/bitmaintech/ltc_frimware inside.
Alternatively, we advise owners of mining farms that run Antminers to set the DNS record on their routers of auth.minerlink.com to 127.0.0.1 in the /etc/hosts file by the following method:
1. Use ssh to login to the miner
2. Run command: echo “127.0.0.1 auth.minerlink.com” >> /etc/hosts
3. Run command: sync
The controversy around this code has brought our attention to improve the design in order to address vulnerabilities that were pointed out by the community recently. For this, we thank the community for pointing out bugs and contributing to our open-source codebase. We would also like to take this opportunity to express our solidified belief in the open source community and express our renewed commitment to improving the quality and testing methods of our code.
We will continue the development of this feature to provide a technical protection for mining rig owners to host their miners in remote locations. We will add a switch to this feature, and this switch will be closed by default. Customers will be able to set up and configure their own authentication server. Before we finish this development, such a code will not be in the firmware we release from now on.
---------------------
Liked this article? Share it with others:





Follow Us for Latest News & Articles:



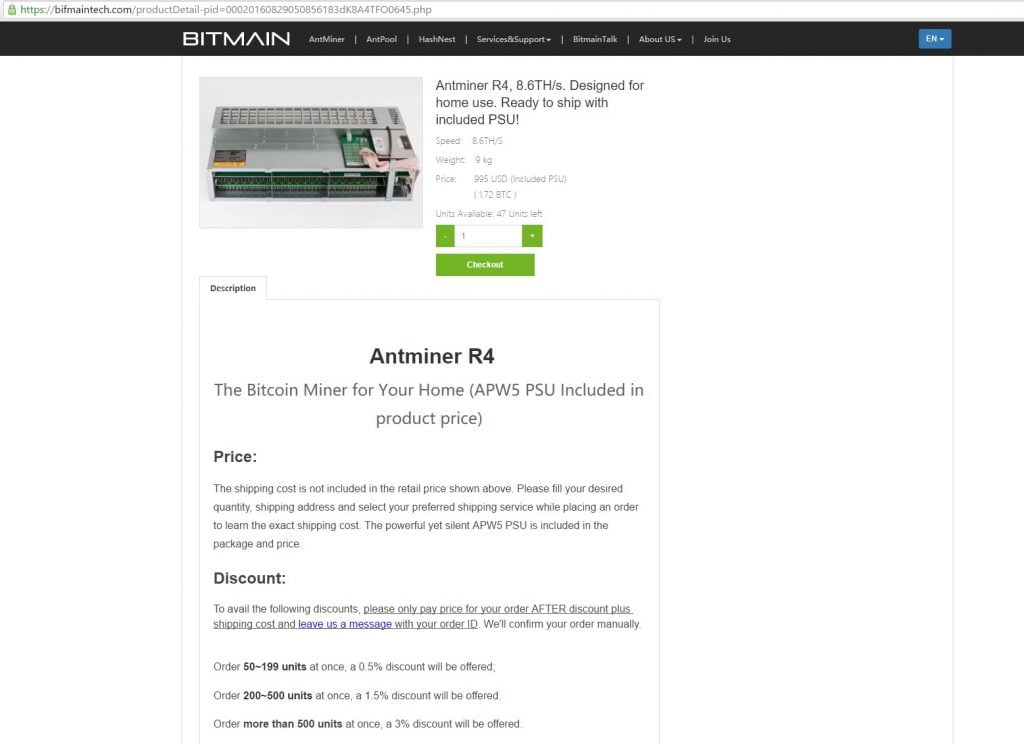 We were today informed by a concerned Bitmain fan that a website with a domain (www.bifmaintech.com) similar to that of Bitmain’s official website www.bitmaintech.com is mirroring our original website. He found this website through a
We were today informed by a concerned Bitmain fan that a website with a domain (www.bifmaintech.com) similar to that of Bitmain’s official website www.bitmaintech.com is mirroring our original website. He found this website through a